What's
Russia’s war with Ukraine in terms of cyber security
Most people think of data theft and hackers when it comes to cyber security. However, as not only recent events in Ukraine have shown, cyber security is part of everyday life. Asset protection in cyberspace is key to the functioning of a country, its industries and services such as energy, transport, healthcare and others. This was also reflected in the current war conflict in Ukraine.
Attacks on Ukraine
In cyberspace, Ukraine has been a target of cyber attacks for several years. An example is the NotPetya attack in 2018, which was attributed to the Russian army [Source].
The military aggression itself was preceded by a new malware attack from February 23 to 24 – HermeticWiper [Source]. Its target was primarily government and financial institutions in Ukraine, but also in Lithuania and Latvia. The attack was insidious because in some cases it used GoLang ransomware as a decoy. While the security components solved the ransomware problem, in the meanwhile HermeticWiper erased all the data in the background, including the MBR part of the disk, which helps to start the operating system. The attack was planned long in advance as Eset found out [Source] that the wiper was compiled on December 28. In one case, Symantec found that attackers exploiting this vulnerability gained access to the networks as early as November 2021.
Since then, organizations and companies in Ukraine have been exposed to a large number of attacks, including phishing attacks on their soldiers [Source]. Compromised devices can be misused to spy on and demoralize troops by sending propaganda messages. On March 3, another attack was recorded to demoralize the population. Hackers hacked the websites of some local governments in Ukraine and posted fake news about Kiev’s surrender or peace with Moscow [Source].
Hacker groups choose sides
World leaders, with a few exceptions, have stood up for Ukraine. Hacker groups have also chosen their side in the ongoing Russian-Ukrainian conflict.
The cybercrime market Raidforums has announced that it has banned access from the Russian Federation. But FSB e-mails and hashed passwords can also be found in the forum [Source].
Anonymous has also joined the Ukrainian side, announcing Operation #OpRussia, which aims to disrupt government and pro-government agencies and companies. The Ghostsec group, which became known for its attacks on ISIS websites that promoted Islamic extremism, also sided with Ukraine. They have caused the failure of more than 100 domains and subdomains associated with the Russian Ministry of Defense [Source].
On the other side of the cyber barricade there are at least 5 groups [Source]:
- UNC1151 – APT (Advanced Persistent Threat) group, which is affiliated with the Belarussian government. Some of its members are also members of the Ministry of Defense of Belarus. Thus, Belarus is also actively involved in this conflict.
- SandWorm – this group is known for its Cyclops Blinks malware and ties to the Russian government.
- The Red Bandits, which (among other things) hacked the onboard cameras of the Ukrainian police [Source]. There is a controversy over whether this group is de facto some kind of Russian intelligence service.
- Coomingproject – an international hacking group has signed up to support the Russian government [Source]. On February 27, another group appeared to have obtained sensitive information and passed it on to police authorities [Source].
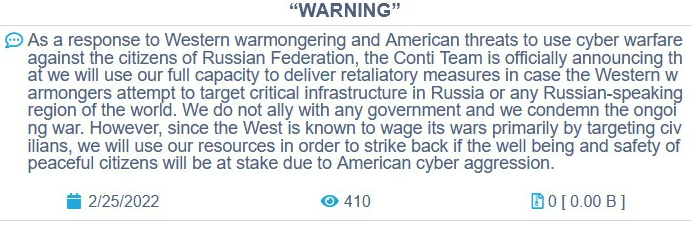
Conti, one of the most active ransomware groups, is responsible for hundreds of millions of dollars in damages. This is the first group to actively exploit the Log4Shell vulnerability.
Development of a position of the Conti group is Interesting. At first the group published a relatively strong statement.
However, an hour later, they replaced it with a milder statement and moved more into the role of defenders of the Russian people. The change was caused by the disapproval of some of its members.
Ukraine and the world respond to cyber risks and attacks
Ukrainian security researcher Vitali Kremez has gained access to more than 60,000 internal reports of the Conti ransomware gang, which he published [Source]. He managed to access their backup database for the XMPP chat server. Conversations describe various gang activities, including private URLs, bitcoin addresses, and discussion of operations. Another leak followed on 1 March, in which their internal files were also leaked [Source].Leakage of such information can seriously affect the activities of this gang.
Ukraine is also recruiting into its volunteer “IT army” of security experts and hackers around the world. Ukraine’s Digital Transformation Minister Mykhailo Fedorov has posted a call on Twitter. A list of 31 targets was created, which includes Russian government agencies, government IP addresses, government repositories or mail servers, three banks and large corporations supporting Russia’s critical infrastructure. Even the popular search engine and mail server Yandex is on the list. One of the less traditional proposals for the “IT army” on their Telegram account is to share videos from the attacks on Ukraine on social networks and possibly pay for advertising these posts in order to spread the information faster [Source].
Meanwhile, Europe is preparing for Russia’s cyber attacks [Source], which are likely to rise. The media, which report on what is happening in the war, are among the endangered. The Slovak public television RTVS has already reported DDoS attacks on its news website [Source]. The Czech Television [Source] was attacked even before the conflict broke out. The Czech National Cyber and Information Security Agency warned about this attack.
The US president was presented with the possibility of a massive cyber attack on Russia in order to disrupt their ability to lead the invasion of Ukraine. The final decision has not yet been made [Source].
Hacktivism
Since the Russian Federation has attacked Ukraine, there has been a large wave of so-called “Hacktivism”. Hacktivism is the term describing the use of computing for activities such as hacking as a form of civil disobedience, pressure to promote social change. The war in cyberspace is different in that, in addition to the official political groups and state armies, various criminal groups as well as civil society can take an active part in the conflicts.
The aim of the ongoing operation #OpRussia of the Anonymous group is to disrupt Russia’s ability to spread propaganda abroad as well as in Russia. It is trying to disrupt the activities of the war-related Russian institutions (government, government agency, media, large corporations). The most commonly used are DDoS attacks, which are gaining strength with the greater involvement of ordinary people. The Anonymous group is extremely active and has declared a cyber war on Russia.
On February 25, RT.com, the Kremlin, the Russian government and the Russian Ministry of Defense were decommissioned by Anonymous [Source]. Later, the group hacked the Russian Ministry of Defense and gained contacts to the people in the ministry, along with their phone numbers, emails and passwords [Source].
Anonymous hackers not only shut down and restrict Russia’s sites, but also use Russian networks to spread their own content, such as authentic footage from Ukraine and the fightings. The aim of these activities is to inform Russian citizens about the activities of their government.
On February 26, Russian state television sites were hacked. Uncensored footage from Ukraine and Ukrainian songs were broadcast on Russian programs [Source]. They managed to obtain 200GB of e-mails from a Belarusian arms supplier that provides logistical support to the Russian troops on Belarusian territory [Source]. According to unconfirmed sources, there are also lists of Russian agents in this leak [Source]. Anonymous captures the communication of the Russian army [Source].
On February 27, Anonymous summarized the results so far. DDoS attacks have affected more than 300 government agencies, state-controlled media and banks, and most have been offline in the last 48 hours [Source].
On February 28, an attack on the Belarusian railways caused the collapse of their computer network. They had to switch to manual control, which slowed down train movements [Source].
Among the hacked sites was the Roskosmos agency’s website [Source], where on March 1 hackers posted information that they had shut down its control centre [Source], which would have caused the loss of information from some satellites.
How not to be a “hacker”
Hacking can seem like something that anyone with the right link or code can do. However, for Slovakia, SK-CERT issued a warning [Source] that “in connection with the war in Ukraine, there were calls in the Slovak cyberspace for distributed attacks on websites in Russia, using a simple web link that the” candidate “should keep open in the browser. “However, the sites do not have to attack Russian sites as they claim, but on the contrary, they could attack Ukrainian sites. Users of this site may also become a victim of malware. In addition, this activity may be against the law.
If a person decides to go to the margins of the law and use such links, then they should at least verify their activity. An easy way to do this is to write “view-source” just before the link (“view-source:https: //www.stranka.com”).
The result of reckless “hacking” with unverified links can be that the “hacker” will put himself in danger. The target of the attack, in this case the Russian institutions, can obtain basic information about the attacker, such as their IP address (in large attacks, however, it is a problem to analyze and draw consequences for all IP addresses).
Under normal circumstances, attackers most often disguise themselves using a VPN or proxy server. There are also free VPNs available, for example in Opera. Another commonly used masking option is to use the TOR browser. Private browsing mode is ineffective in this case and does not affect the attacker’s masking.
Two worlds, two approaches
The ongoing DDoS attacks on targets in Russian cyberspace have a twofold effect. They make it difficult for the pro-Russian media and the government to use propaganda, and they serve to bind IT professionals who must defend these institutions from those attacks and cannot engage in other activities. However, more sophisticated attacks are also taking place in the background, leading to leaks of sensitive data. They are not easily identifiable in this large wave of attack traffic.
Russia has one of the largest cyber armies. It carried out several very insidious attacks, especially on Ukraine. For example, they cut off electricity for 230,000 people. There is a concern about what will happen when they attack the US or one of the EU countries in this way. This is one of the reasons why national authorities publish warnings against such attacks (eg: Slovakia, the Czech Republic).
Cyber armies can focus on attacking or defending. They all have the same resources (computer networks, operating systems, etc.), so as an attacker attacks, he can also be attacked in the same way. This is especially true for the so-called zero-day vulnerabilities (unknown vulnerabilities until now). Intelligence agencies do not report software vulnerabilities too often because they would limit their attack potential. It is likely that Russia is technologically similar to the US a few years ago, also because it focuses on offensive activities [Source].
However, with the establishment of CISA, the US began to significantly improve its defense capabilities. The application of classic rules also helped – regular system updates, monitoring of activities, staff training, or issuing guidelines. The fact that cyber security has become one of the priorities of the acting US President has also made a significant contribution [Source]. As a result, they should be more protected.
We do not know about such a large-scale defense initiative in Russia. However, this does not mean that they are not doing anything, because Russian activities are usually not communicated at all, while the US publishes at least some of its actions.
Approach to cyber security personnel is also different. The US relies on its secret services (primarily the NSA) and possibly government contractors (often companies of former NSA agents). Russia has such divisions within its secret services (especially the GRU and FSB) and can also use the services of cyber criminal gangs. These gangs have more or less guaranteed impunity on Russian soil. Their conditions are that “they will not attack at home” and that when the government turns to them, they are expected to cooperate [Source].
Slovak cyberspace is protected also by NATO, specifically the Cooperative Cyber Defense Center of Excellence, in which experts from Slovakia also participate. However, it is still the case that the prevention carried out by each entity internally is irreplaceable. For example, the Slovak authority SK-CERT publishes tips on how to maintain cyber security in every organization.